Microsoft Ignite 2024 guide: Cloud observability for AI transformation
Dynatrace
NOVEMBER 18, 2024
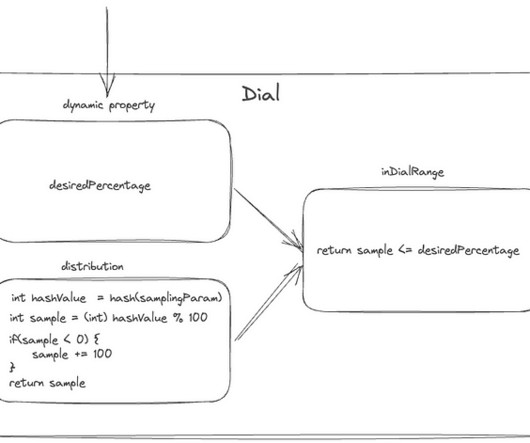
Read on to learn more about how Dynatrace and Microsoft leverage AI to transform modern cloud strategies. Race to the cloud As cloud technologies continue to dominate the business landscape, organizations need to adopt a cloud-first strategy to keep pace.



































Let's personalize your content