Transforming Telecom With AI/ML: A Deep Dive Into Smart Networks
DZone
DECEMBER 28, 2023
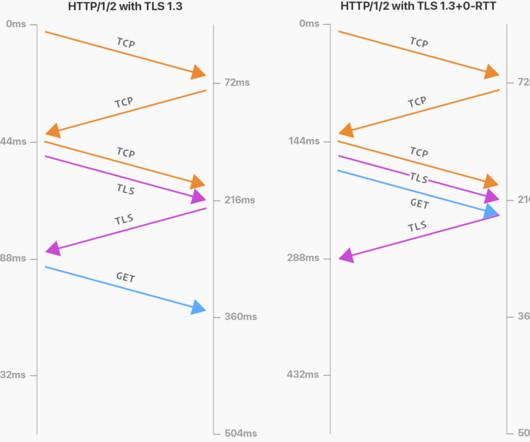
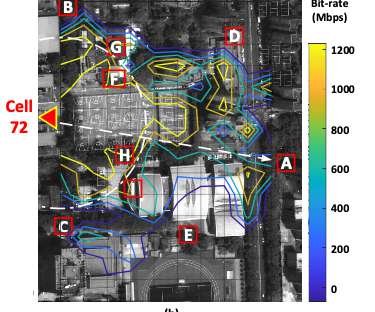
The telecommunications industry has become an indispensable part of our interconnected society, fueling various functions ranging from traditional calls to lightning-fast Internet and the ever-expanding Internet of Things ( IoT ). Here's an example of how machine learning can optimize network performance:


































Let's personalize your content