Microsoft Ignite 2024 guide: Cloud observability for AI transformation
Dynatrace
NOVEMBER 18, 2024
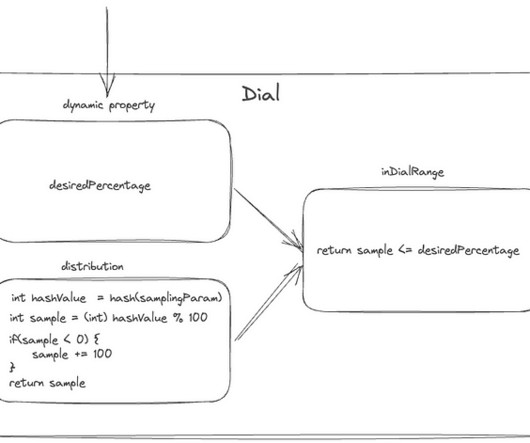
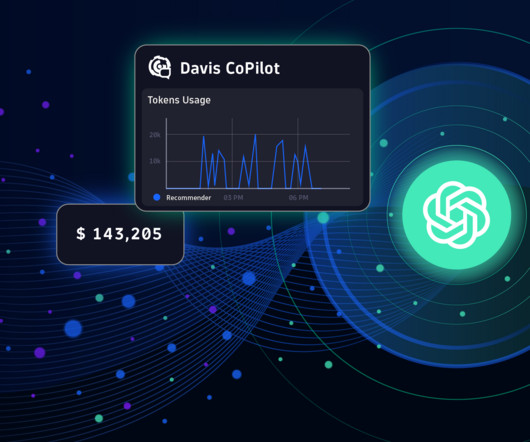
Adopting AI to enhance efficiency and boost productivity is critical in a time of exploding data, cloud complexities, and disparate technologies. Read on to learn more about how Dynatrace and Microsoft leverage AI to transform modern cloud strategies.




































Let's personalize your content