Vulnerability assessment: key to protecting applications and infrastructure
Dynatrace
OCTOBER 13, 2021
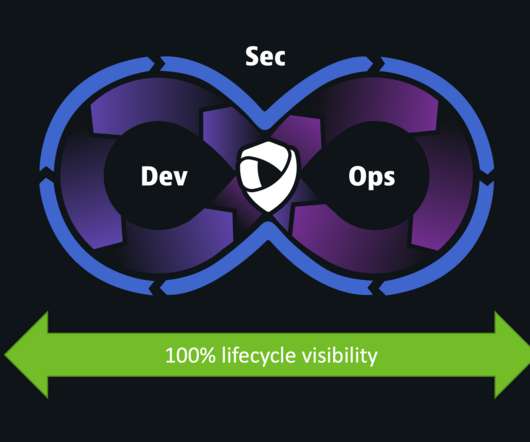
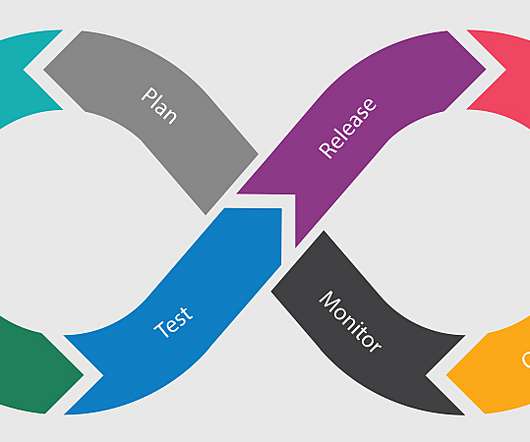
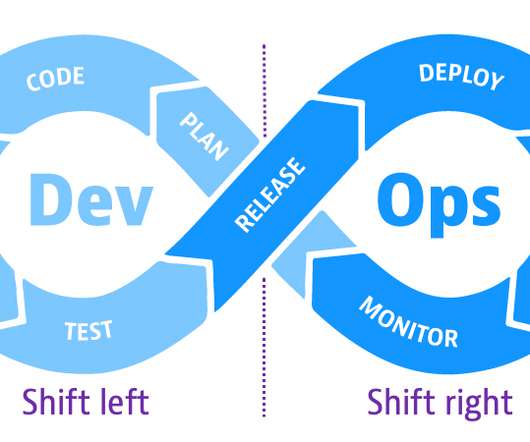
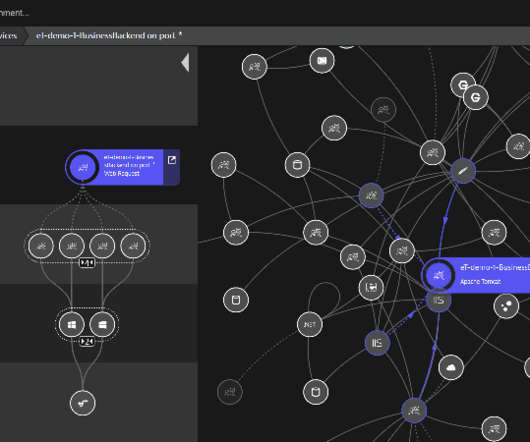
Protecting IT infrastructure, applications, and data requires that you understand security weaknesses attackers can exploit. Cloud infrastructure analysis ensures the secure configuration of cloud infrastructure including virtual machines, containers, cloud-hosted databases, and serverless services. Dynatrace news.









































Let's personalize your content