Efficient SLO event integration powers successful AIOps
Dynatrace
APRIL 5, 2024
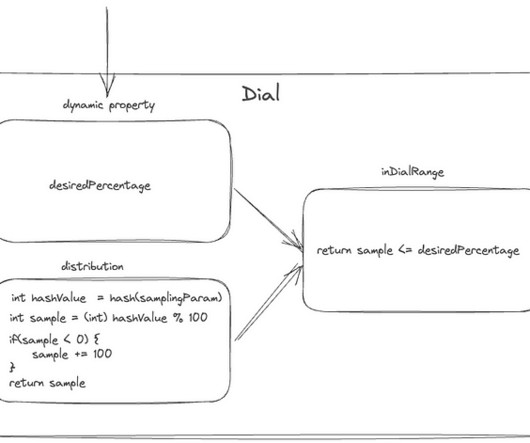
In other words, where the application code resides. This implies that when the status is unfavorable, implementing sophisticated alerting methods like error budget burn rate alerting presents challenges and is therefore not applicable. Interested in learning more? Contact us for a free demo.


































Let's personalize your content