The top eight DevSecOps trends in 2022
Dynatrace
FEBRUARY 23, 2022
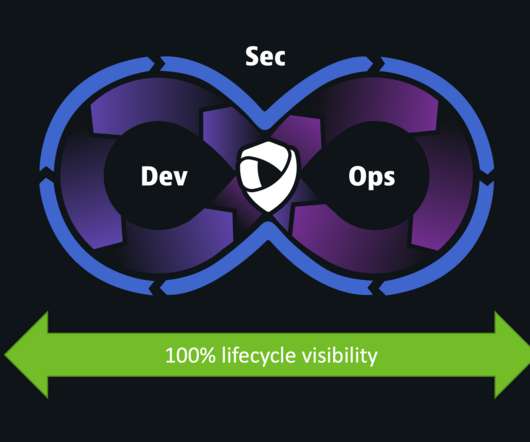
Incorporating DevSecOps practices can bring security, compliance, and development discipline to organizations seeking to move faster without sacrificing code quality: According to one survey, 96% of respondents said their organization would benefit from automating security and compliance processes , a key principle of DevSecOps.







Let's personalize your content