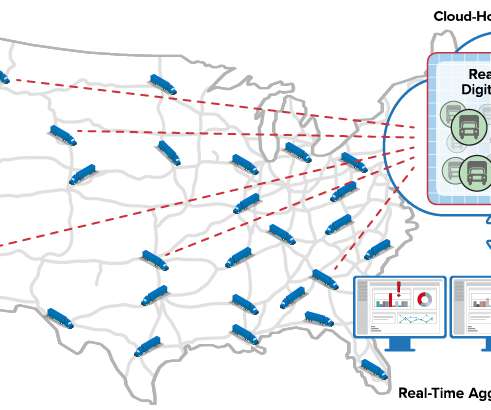
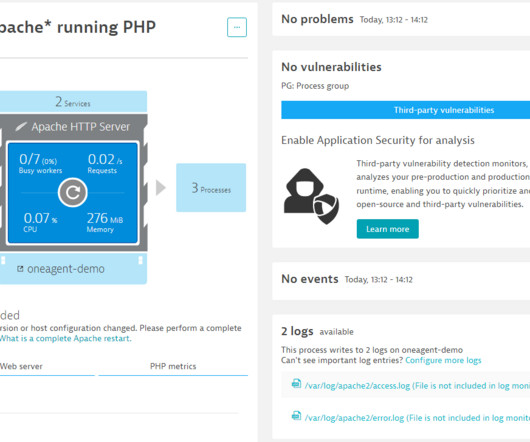
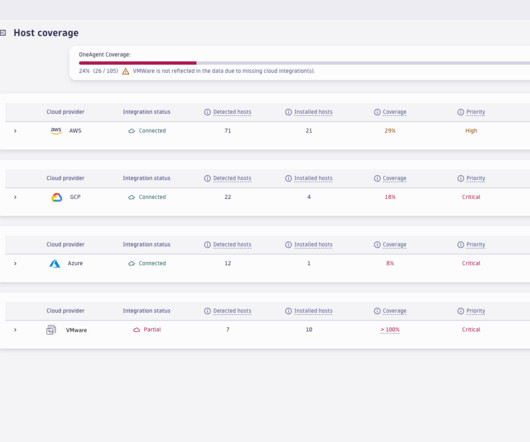
Vulnerability assessment: key to protecting applications and infrastructure
Dynatrace
OCTOBER 13, 2021
Examples of such weaknesses are errors in application code, misconfigured network devices, and overly permissive access controls in a database. In all, there are seven types of vulnerability assessments, each with its own focus and methods: Application analysis has two types: static and dynamic. Analyze findings.






































Let's personalize your content